Over the past years, I wrote a book on Quantum Computing for Manning Publications: Quantum Computing in Action.
I also wrote a Quantum Computing simulator in Java, named Strange.
In this article, I discuss a very basic approach of using quantum computing to improve network security. I briefly explain the concepts, and in a next article I plan to show real code that explains it in practice. I won’t go into details though. For more information about Quantum Computing and how it can be used together with classical computing, I highly recommend my book “Quantum Computing in Action”.
Quantum Computing offers a number of ways to make digital communication more secure. One of the main challenges in digital communication, where digital bits (a series of bits that are either 0 or 1) are sent from one computer to another, is that one should accept that those bits might be intercepted, and read/altered during communication over a physical carrier. However, the communication is necessary in order to transfer information.
In the following picture, Alice and Bob each have their own device (e.g. a laptop or a phone) and Alice wants to send a message to Bob by sending bits over the Internet.
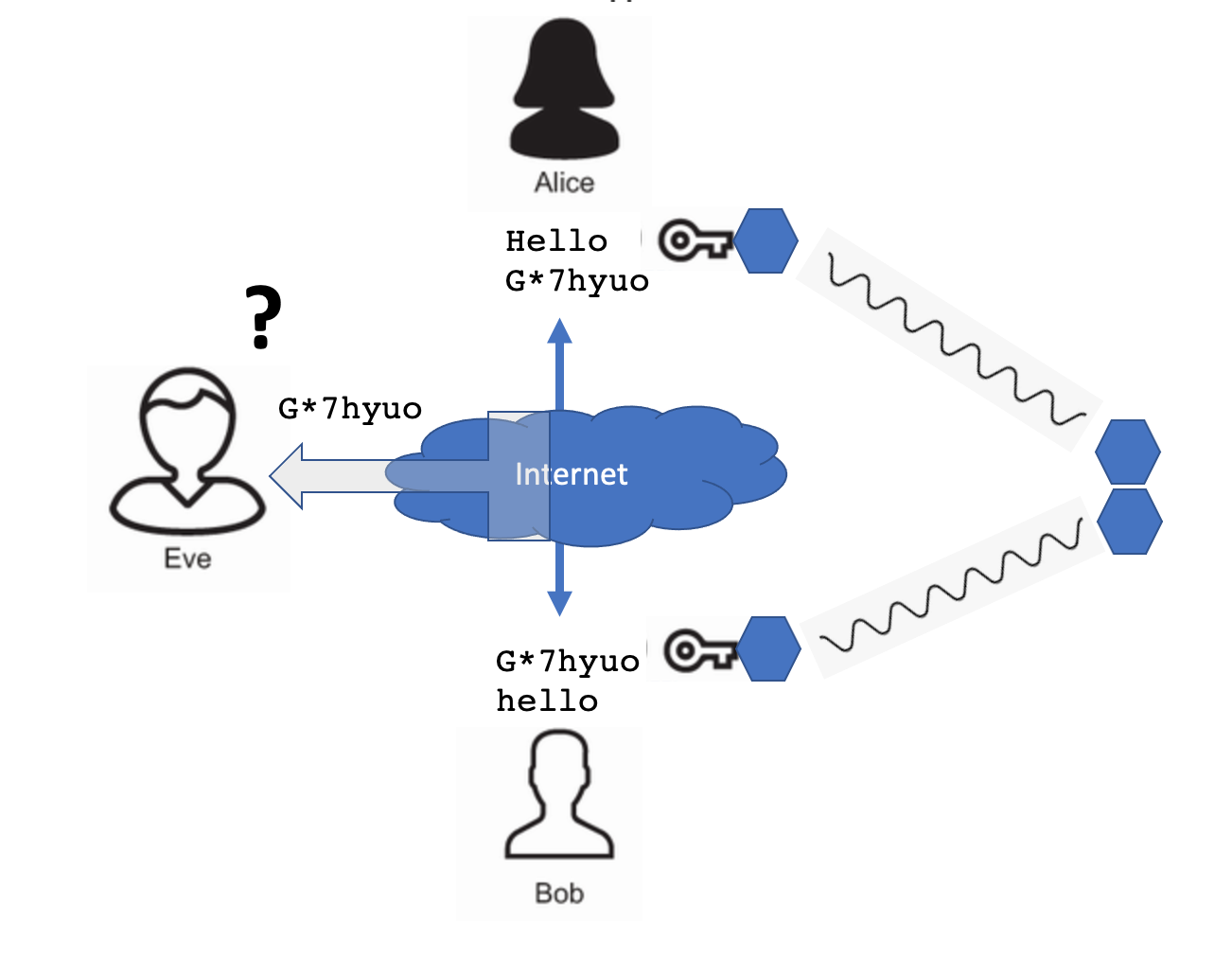
The information flow between Alice and Bob uses wireless routers, fiber cables, routers,… and it should be assumed that whatever is sent over these channels might be read by third parties, e.g. Eve:

Since Alice and Bob don’t want Eve to read their conversation, they encrypt their messages before they send them over the internet. One of the popular approach to do this is to have Alice and Bob using a shared secret: a key that both of them know, but nobody else knows. A great example of how a shared secret can be created is the Diffie-Hellman key exchange algorithm (see https://en.wikipedia.org/wiki/Diffie%E2%80%93Hellman_key_exchange).
When Eve intercepts the encrypted message, she can’t make sense of it since she doesn’t have the key Alice and Bob are sharing.

One of the intriguing aspects of quantum physics is that nature gives us the concept of a shared secret as well, through the concept of superposition and entanglement. (see chapters 4 and 5 of https://www.manning.com/books/quantum-computing-in-action). Translated to computing and networking, this means that it is possible to generate 2 entangled qubits, and send them to 2 different devices (e.g. Alice and Bob). These qubits are initially in a Bell State, which means that they are in a superposition and entangled state. They both hold the values 0 and 1 simultaneously, and only when one of the qubits is measured, they “choose” a value of either 0 and 1. You can find much more background and info in my book, but the key idea here is that when Alice measures her part of the entangled qubit, it determines not only the value of her qubit, but also the value of Bob’s qubit. Alice and Bob do not need to send information over a classical line, since Bob’s qubit already “knows” the state of Alice’s qubit. If you think this is spooky and hardly possible since this seems to allow a transfer of information faster than light, you’re not alone. Even Einstein struggled with this concept (see https://en.wikipedia.org/wiki/EPR_paradox) .
Once Alice and Bob each hold a qubit with the same value, only known to them, they can use that value to generate a shared secret and apply many existing encryption technologies.
An important question is then: “How can Alice and Bob each obtain a part of an entangled pair?” It turns out that this is already possible today, over limited distances, and with limited nodes. It is especially worth mentioning the work of QuTech in Delft, where lots of research is done related to quantum networking. See for example https://qutech.nl/2021/04/15/dutch-researchers-establish-the-first-entanglement-based-quantum-network/ .
While the equipment to generate entangled qubits and transmit them over network infrastructure to different nodes is not yet widely available, it is very well possible to simulate this using Quantum Simulators, e.g. Strange, the quantum computing simulator I wrote in Java.
In a next post, I will show code that uses this simulator to transmit bits from Alice to Bob, encrypted using entangled qubits.
Continue reading here: https://johanvos.wordpress.com/2022/03/30/a-java-approach-for-leveraging-quantum-entanglement-in-communication/
